With the vast number of login credentials and accounts created each day, malicious actors are continually seeking ways to exploit these surfaces to gain unauthorized access. Among the various methods available, “one luck-based” technique stands out (brute-forcing).
One luck-based method of exploiting login pages is brute forcing, which involves trying multiple combinations of usernames and passwords to gain unauthorized access to an account or system. The term “luck-based” refers to the probability that the correct credentials will eventually be guessed.
Brute-forcing relies heavily on the hacker’s persistence and ability to generate a multitude of potential password combinations.

This approach may use weak passwords, such as dictionary words or easily guessable patterns, and can be accelerated with specialized tools or algorithms.
While brute-force attacks are time-consuming and may not guarantee success, they represent a genuine risk to the security of login pages, particularly for those with weak or predictable password policies.
Understanding Login Pages
Components of Login Pages
Login pages typically consist of a form with essential fields that users must fill in to access a website or application. The primary components of login pages include:
- Username: A unique identifier that represents a specific user. Usernames can be an email address, a nickname, or any other string of characters.
- Password: A secret string of characters, known only to the user, that provides a security measure for their account. Passwords should be strong, containing a mix of uppercase and lowercase letters, numbers, and symbols.
- Login Button: A button that triggers the authentication process when clicked. This button is used to submit the provided username and password for verification.
Main Purpose
The primary purpose of login pages is to authenticate users by verifying their identity before granting access to a website or application’s protected resources. The process typically involves:
- The user enters their username and password on the login page and then clicks the login button.
- The entered credentials are sent securely to the server for verification.
- The server checks the provided username and password against the stored data. If a match is found, it implies the user’s identity is confirmed, and access to protected resources is granted.
- If the credentials do not match, the user is denied access and may be prompted to try again or reset their password.
Common Vulnerabilities on Login Pages
SQL Injection
This technique involves injecting malicious SQL code into user input fields, such as username and password fields, to gain unauthorized access to an application’s database.
An attacker may use this vulnerability to retrieve sensitive information (e.g., user credentials) or alter the application’s behavior.
To mitigate the risk of SQL injection attacks, developers should use parameterized queries and input validation to sanitize user inputs.
Brute Force Attacks
As we said earlier, A brute force attack is a luck-based method of exploiting login pages by systematically attempting numerous username and password combinations until successful access is granted.
This method can be time-consuming and resource-intensive, but it may ultimately yield unauthorized access (especially if weak or default passwords are used).
Although intruder lockout mechanisms can help mitigate brute force attacks, they are not always implemented in applications.
Credential Stuffing
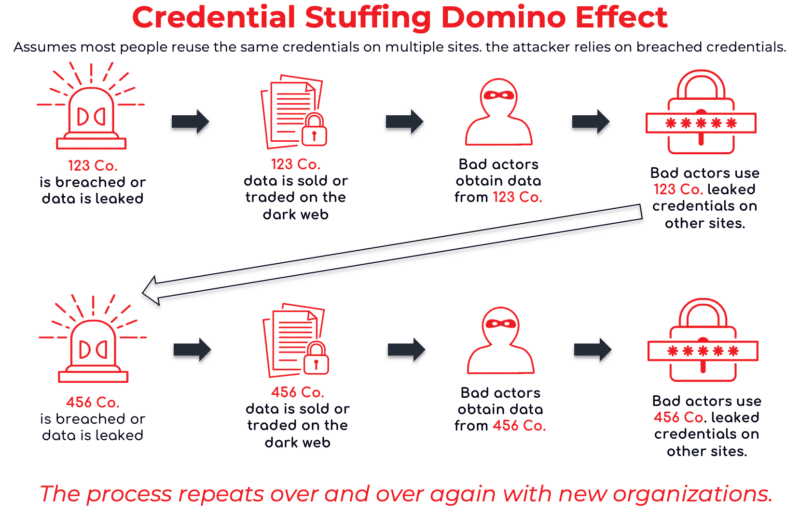
Credential stuffing is an attack technique where an adversary attempts to gain unauthorized access to a login page using previously obtained credential pairs (e.g., data breaches or leaks). Since users often reuse their login credentials across different services, adversaries exploit this pattern to compromise multiple accounts.
Phishing
Phishing attacks target login pages by tricking users into divulging their login credentials through deceptive methods, such as creating fake login pages or sending malicious emails requesting a password reset. These tactics prey on users’ trust, often duping them into revealing sensitive information to malicious actors.
Luck-Based Methods: Trial and Error
Guessing Usernames and Passwords

One luck-based method of exploiting login pages is trial and error. In this approach, an attacker attempts to gain unauthorized access to an account by guessing usernames and passwords.
The trial and error method involves making multiple attempts until the correct username and password combination is found or the attacker decides to stop.
Attackers might target common usernames, such as “admin” or “administrator,” and try a list of commonly used passwords. They may even try email addresses as usernames, considering many platforms use them for account identification.
This method relies on the probability of finding a weak combination of username and password that lacks appropriate security measures.
Using Wordlists for Attempts
To increase the chances of success, an attacker can employ wordlists in their trial and error approach. Wordlists are pre-compiled lists of words and phrases, often collected from sources such as leaked password databases, dictionary files, and commonly used password patterns.
Using wordlists, attackers can automate their attempts to exploit login pages through techniques such as brute force attacks and credential stuffing.
Brute force attacks involve systematically trying every possible password combination until the correct one is found, while credential stuffing involves using previously breached or leaked credentials in the hope that a user has reused the same password across multiple platforms.
Exploiting Directory Listings
Discovering Hidden Directories
Hackers may use various tools to uncover hidden web directories when attempting to exploit login pages. One such luck-based method is brute-forcing, which entails trying different combinations of characters to guess the correct credentials or discover vulnerable directories (source). Tools like Gobuster and Dirb can help automate this process on Linux systems.
Gobuster identifies hidden directories by sending HTTP(S) requests to the specified URL, looking for 404 Not Found errors, indicating that a requested resource is not on the server. To discover directories using Gobuster, you can use the dir switch, like this:
gobuster dir -u https://target-website.com -w /path/to/wordlist
This command will send requests to the target website (using the specified wordlist) and identify which directories exist based on the server’s response codes, such as 404 for “Not Found” or 443 for secure HTTP over SSL/TLS (HTTPS) (source).
Identifying Key Files

Once hidden directories are discovered, a hacker may look for critical or sensitive files, like configuration files, password lists, or user information. The attacker may rely on manual inspection, automated file discovery tools, or both methods.
Some useful techniques for locating key files include:
- Directory traversal: Exploring the found directories by navigating through the directory tree and looking for files that could contain sensitive information.
- File extension filtering: Identifying files with specific extensions, for example,
.txt,.conf, or.json, which may contain essential configurations or data. - Analyzing file permissions: Using operating system utilities (Linux
ls, For example) to check file permissions, looking for files with weak or no access control.
Additionally, an attacker may leverage the target server’s IP address to gather more information, such as server type, location, and other services running on the same IP. This knowledge may help an attacker to craft more sophisticated strategies to exploit identified weaknesses in the login page and directories.
Brute force attack prevention
To safeguard against brute-force attacks, it is imperative for both users and developers to implement robust security measures. Users should create strong, unique passwords that are not easily guessable, while developers must enforce stringent password policies and employ added layers of protection, such as multi-factor authentication or account lockouts after a designated number of failed login attempts.
By staying vigilant and adopting these defenses, the chances of a successful brute-force attack can be significantly reduced, thus enhancing the overall security posture of login pages.
Having read the above instructions, you must understand that it is essential for security professionals and developers to safeguard web applications against attacks targeting login pages. You must understand and anticipate “Brute-force” attempts. Develop and implement a robust security framework to mitigate threats and protect your users’ sensitive information.
