Jumping straight to Hackthebox as a total cybersecurity beginner could be intimidating. Some may even argue that you should start with Tryhackme before even thinking about touching Hackthebox. But fear not because not only will I get you excited about Hackthebox today, but you will also be able to kick the entire Hackthebox Tier 0 machines.
Starting Point is a series of beginner-friendly Hackthebox machines. It consists of three tiers, from Tier Zero to Two. The goal is to find a specific file named “user.txt and a root.txt.” They contain a short string that represents the so-called “flag.”
Although the Starting Point Tier 0 is as beginner as you get in Hackthebox, don’t let the “Very Easy” under all those machines fool you. Many people still find them to be tough to get done. This is why we will see the good and the wrong way to learn in Hackthebox.
Getting Started with Hackthebox Starting Point Tier 0
Starting Point Tier 0
Hackthebox Tier 0 is the first level of challenges in the Starting Point series. It is designed to teach users the basics of cybersecurity and penetration testing, as well as familiarize them with the Hackthebox platform.
How to Access Hackthebox Starting Point Tier 0?
To access Hackthebox Starting Point Tier 0, you must sign up for an account on the Hackthebox website. Once you have created an account, you can access the Starting Point challenges and virtual machines.
Prerequisites
To get the most out of Hackthebox Starting Point Tier 0, you should have a basic understanding of networking, Linux, and cybersecurity concepts. In addition, the Linux shell command line is a must and a particular emphasis on text manipulation is worth pointing out.
Is it okay to use HacktheBox writeups Walkthrough?

Believe it or not, this is the most recurrent question asked by beginners and Medium level folks about doing Hackthebox Machines. Unfortunately, beginners feel like they are cheating themselves by having recourse to Writeups, google, and watching a youtube video on how to solve machines.
Here’s my response to this question. First, while it is okay to use Hackthebox Walkthroughs, I recommend you try to use the writeups as little as possible.
Try harder! My tip is to try everything you know before using writeups. Read only the top lines of the writeup to understand the instructions thoroughly. But as soon as you do, get back to the lab and try to solve everything yourself first.
Walkthrough of Hackthebox Starting Point Tier 0
As of now, the Starting Point Tier 0 consists of Nine machines. The first four are free, but the rest require a VIP subscription.
In this article, we will only focus on the first machine, “Meow.” If you want a full breakdown of all Starting Point machines, visit the link here.
Meow
Step 1: Connecting to the VPN
First, ensure you have an active connection with the target’s network. See this article for further explanation of this process.
You get two choices here:
a) PwnBox Connection:
PwnBox lets you connect directly to the target machine. No additional steps are required. You will automatically be placed in the same network as the target if you choose the Starting Point option when booting up a new Pwnbox instance.
b) OpenVPN: The free option and the one I will recommend using the most.
Click on the starting Point link and download the “OpenVPN” Files.
Click to download the VPN (.ovpn) configuration file. Then open the terminal icon on your Desktop.
In the terminal, navigate to the Download directory, type in ls to ensure the “.ovpn” file is on the system, then type in the following command to launch your OpenVPN client and connect to the Hackthebox internal network.
sudo openvpn {filename}. Like so:
sudo openvpn {filename}. Like so:
┌──(kali㉿kali)-[~]
└─$ cd Downloads┌──(kali㉿kali)-[~/Downloads]
└─$ ls
‘starting_point_atouba64(1).ovpn’ starting_point_atouba64.ovpn┌──(kali㉿kali)-[~/Downloads]
└─$ sudo openvpn starting_point_atouba64.ovpn
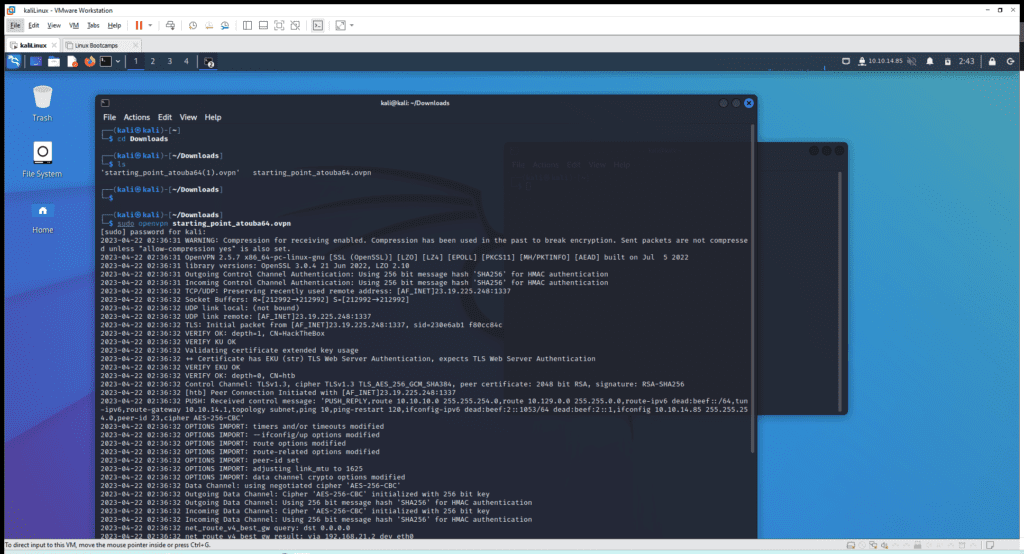
Note: I will suggest you leave the instance with the command “sudo openvpn starting_point_atouba64.ovpn” open. And open another Terminal instance to carry on with the rest of the tasks.
And you may lose connection to the remote machine from time to time. So it’s always a good idea to ping it every 5 minutes. If you get replies, that’s wonderful. But if not, try to retype “sudo openvpn starting_point_atouba64.ovpn” once more to reconnect to the remote machine.
Then, you should see the following on your next to “Connect” under your Machine’s Tasks.
Step 2: Click on Spawn the Machine
Further down the page, you should see question two with an option to spawn the box. Click on the spawn the box link, and it should do just that. Additionally, once the box has been spawned, you should see an IP address. Essentially, this is the address for the box that we will use to communicate with it.
Step 3: Complete the different tasks
It’s now fun time! You get to answer all the tasks and capture the flag.
Task 1:
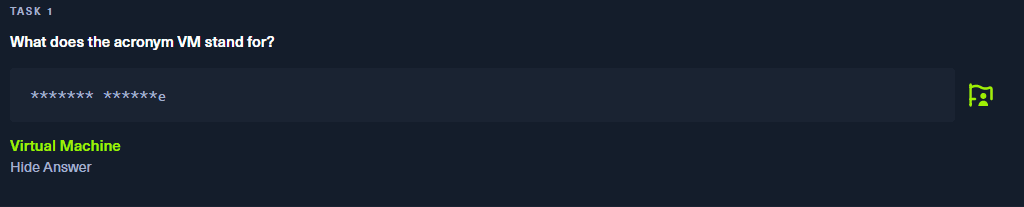
What does the acronym VM stand for?
Taks 2:
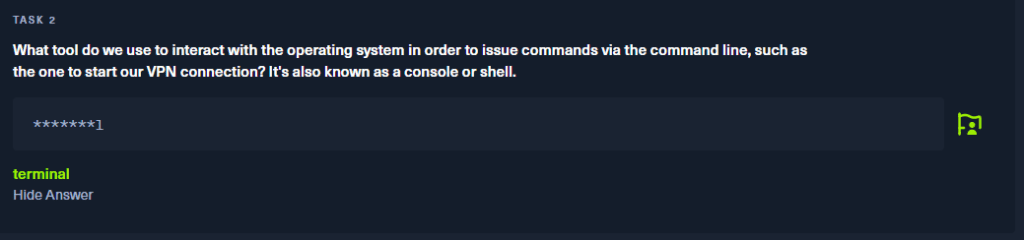
What tool do we use to interact with the operating system in order to issue commands via the command line, such as the one to start our VPN connection? It’s also known as a console or shell.
Task 3:
What service do we use to form our VPN connection into HTB labs?
Task 4:
What is the abbreviated name for a ‘tunnel interface’ in the output of your VPN boot-up sequence output?
You can find this information by running the “ifconfig” command on your virtual machine. I snipped out my eth0 and loopback address and some other information, but you can see that the abbreviated name is tun0.
┌──(kali㉿kali)-[/media/sf_OneDrive/Hack The Box/Machines/Meow]
└─$ ifconfig
tun0: flags=4305<UP,POINTOPOINT,RUNNING,NOARP,MULTICAST> mtu 1500
inet 10.10.15.119 netmask 255.255.254.0 destination 10.10.15.119
Task 5:
What tool do we use to test our connection to the target with an ICMP echo request?
Use the ping command here. And after four successful replies from the target, we can determine that our connection is formed and stable. We can cancel the ping command by pressing the CTRL+C combination on our keyboard.
Task 6:
What is the name of the most common tool for finding open ports on a target?
In order to get this information. You will need to run the Nmap like so:
sudo nmap -sC -sV -p- 10.129.122.207
Nmap stands for Network Mapper. This command will scan all of the target’s open ports to determine the name and description of the identified services (-sV).
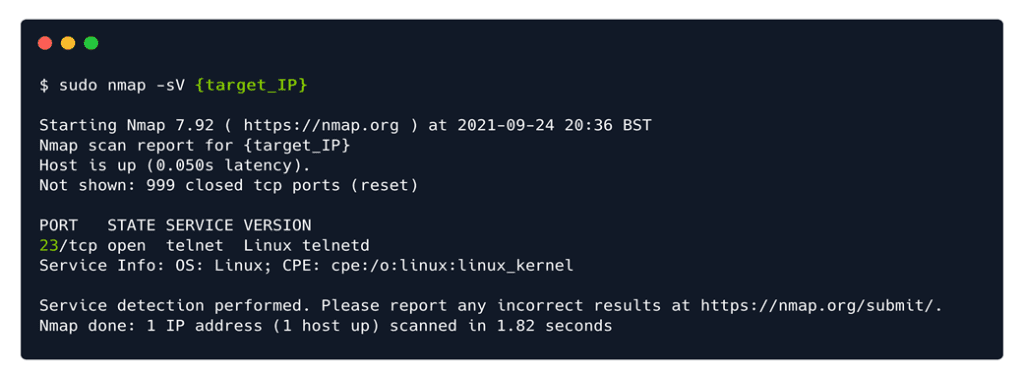
After the completion of the scan, we identify port 23/tcp as “open.” Port 23 is associated with Telnet. We can then also answer the following up question.
Task 7:
What service do we identify on port 23/TCP during our scans?
Task 8:
What username is able to log into the target over telnet with a blank password?
Usually, connection requests through Telnet are configured with username/password combinations for increased security. It will then show you the “HackTheBox” banner and a request from the target to authenticate ourselves.

We will then use “root” as the username and a blank password in order to authenticate ourselves.
And now that we have successfully logged into the target system (remote machine). It’s now time to find the flag.

The flag is a text file located somewhere in the target or remote computer.
Use the “ls” command to look around.

The flag.txt file is our target. (“.txt”). Most of HackTheBox’s targets will have one of these files, which will contain a hash value called “a flag.”
Use the to read the file. Use the “Cat” command like so:
#Cat flag.txt
Copy the file (Flag), and paste it into the Starting Point lab’s page.
And that, my friend, is how you get you’ve just completed your very first Hackthebox machine.
Congratulations!
Tips and Tricks for Hackthebox Starting Point Tier 0
Best Practices
It is important to follow some best practices when getting started to get the most out of Hackthebox Starting Point Tier 0. Before attempting any challenges, read through the instructions and hints provided. This will help you understand what you have to do and what tools you will need.
Secondly, please make a note of the challenges as you overcome them. It will help you keep track of what worked, what didn’t work, and what you still need to try.
It will also help you remember any useful commands and techniques you encounter.
Finally, if you get stuck, feel free to ask for help. Hackthebox is a very helpful and supportive community, and there are many resources available.
Common Mistakes to Avoid
Here’s what I’ve learned from my experience with Hackthebox:
- It’s not a good idea to rush through the challenges. Take your time and be sure that you understand what you’re doing before moving on.
- Try to rely as little as you can on automated tools. Tools such as Nmap and Metasploit are very useful, but try your best to understand them instead of just using them recklessly.
- You will not be able to solve all challenges right away. Don’t get frustrated though. The point of Hackthebox is to teach you skills through real-world challenges and experiences. Just view every single challenge as an opportunity to learn and improve.
Conclusion
Starting Point Tier 0 is the best thing that had ever happened to me in my cybersecurity career. And I hope that it does the same for you. It taught me countless skills and concepts.
But most importantly, it introduced me to the big and wonderful world of other thousands of Hackthebox machines and other Pentesting labs. While the challenges are designed to be challenging, they are not impossible.
With patience, persistence, and dedication, you can overcome them and become a better hacker. Learning in Hackthebox is less obvious than in any other platform. It is an art in itself. An art worth learning, though, because of the tremendous things it teaches and introduces you to.
