
Any attacker needs to gather information about the target infrastructure. DNS enumeration allows one to discover all the DNS servers and records of a particular domain. It can be done manually, but it is a time-consuming process. Hence, it is often automated using tools like Nmap.
Nmap is a highly effective tool for scanning networks that can serve many different purposes, including DNS enumeration. Nmap has a helpful built-in script called “dns-enum” that you can use to perform DNS enumeration.

This script helps find DNS servers and records for a domain, including subdomains, MX records, and other relevant data.
In addition, the “dns-enum” script can also perform zone transfers, revealing sensitive information about the target’s DNS infrastructure.
What is DNS Enumeration?
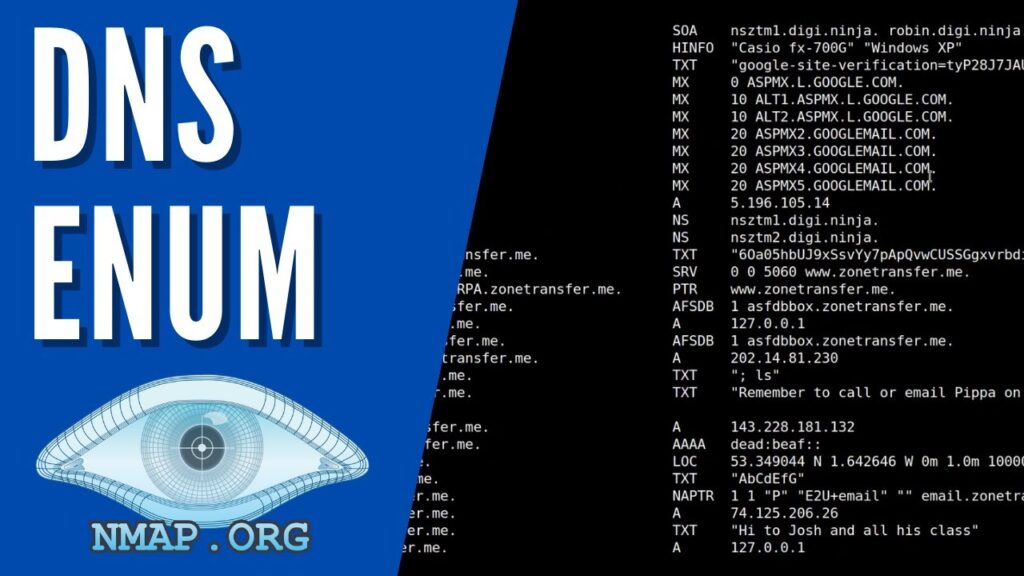
DNS Enumeration refers to gathering information about a target’s domain DNS records. It involves querying a DNS server to extract valuable info about the domain and its network infrastructure. DNS enumeration aims to identify possible entry points to a network and exploit them. For future attacks.
DNS servers translate human-readable domain names into IP addresses that computers can understand. DNS Enumeration reveals crucial network information for attackers to launch further attacks.
There are several ways to perform DNS Enumeration, but one of the most popular tools for this task is Nmap.
During DNS Enumeration, Nmap can be used to query the target network’s DNS servers for information such as:
- Hostnames
- IP addresses
- Mail servers
- Name servers
- Network topology
- Operating systems
After gather this info. You can identify potential targets for further attacks, such as vulnerable hosts or services that can be exploited.
DNS Enumeration has both legitimate and malicious applications. Network administrators may use it to detect potential vulnerabilities and take corrective measures.
However, attackers can also exploit DNS Enumeration to collect information required to initiate attacks against the target network. Hence, Network admins must protect their networks from security breaches.
Why Use Nmap for DNS Enumeration?
The enumeration is the first step of penetration testing engagement. This is where you gather information about the target system or domain
Nmap’s DNS enumeration capabilities make it an excellent tool for this task. Here is why:
- Speed: Performs DNS enumeration quickly and efficiently, allowing for faster reconnaissance and more time for other tasks.
- Accuracy: Nmap’s DNS enumeration is highly accurate, providing detailed information about the target domain’s DNS servers and records.
- Flexibility: Users can customize DNS enumeration with Nmap to fit their needs. It will enable them to search for specific DNS records or enumerate subdomains.
- Integration: Integrating Nmap with tools like Metasploit or Nessus gives a complete view of a domain’s security. It’s easy to integrate them.
Benefits of Using Nmap for DNS Enumeration
Some of the few are:
a) Versatility:
Nmap can be used to scan a wide range of networks, from small local networks to large enterprise-level networks.
Additionally, Nmap can be configured to scan for specific types of DNS records, such as MX, TXT, and SRV records, which can provide valuable information about the network’s infrastructure.
b) Speed and efficiency:

Another advantage of using Nmap for DNS enumeration is its speed and efficiency.
Nmap can scan a network quickly and accurately, allowing administrators to identify potential security vulnerabilities in a timely manner.
This can be particularly important in large networks where manual scanning would be impractical.
Nmap’s DNS enumeration capabilities are constantly improving with new features and enhancements, making it a valuable tool for security professionals and researchers who need to gather information about a target domain’s DNS infrastructure.
These benefits are ever-evolving and worth considering.
How to Use Nmap for DNS Enumeration
Here’s how to use Nmap for DNS enumeration.
- Install Nmap
- Determine the Target DNS Server
- Use Nmap to Enumerate DNS Inforamtion
Step 1: Install Nmap
You need to have Nmap installed on your system. Nmap is available for all major operating systems, including Windows, Linux, and macOS. You can download the latest version of Nmap from the official website.
Step 2: Determine the Target DNS Server
This can be done using tools like nslookup or dig. Once you have the IP address of the target DNS server, you can use Nmap to enumerate DNS information.
Step 3: Use Nmap to Enumerate DNS Information
To use Nmap for DNS enumeration, you can use the following command:
nmap -sS -sU -p 53 --script dns-* <target-IP>
This command will scan the target DNS server for open TCP and UDP ports on port 53 and run all the DNS scripts that come with Nmap. The output will contain all the DNS entries associated with the target domain.
Alternatively, you can use the following command to perform a zone transfer:
nmap -sS -sU -p 53 --script dns-zone-transfer <target-IP>
By executing this command, you can try to perform a zone transfer on the targeted DNS server. In case of a successful transfer, a comprehensive list of all DNS entries linked with the target domain will be provided.
Common Techniques for DNS Enumeration with Nmap

In this section, we will discuss some of the common techniques for DNS enumeration with Nmap.
Zone Transfer
One frequently used method for DNS enumeration is zone transfer, which involves copying the entire DNS zone file from one server to another.
This approach allows the user to obtain a comprehensive list of DNS records for a given domain.
To perform a zone transfer with Nmap, you can use the following command:
nmap -sV --script=dns-zone-transfer <target>
Reverse Lookup Brute Force
Reverse lookup brute force is another technique for DNS enumeration. This technique involves brute-forcing the IP addresses to obtain the corresponding domain names. This process can be used to discover all the subdomains that are associated with a particular IP address.
To perform a reverse lookup brute force with Nmap, you can use the following command:
nmap -sL -n <IP range> | awk '/Nmap scan report/{print $NF}' | xargs -I{} host {}
Forward Lookup Brute Force
Another DNS enumeration technique is called forward lookup brute force. This method uses brute force to find the IP addresses corresponding to a given domain name.
This process makes it possible to uncover all the IP addresses linked to a specific domain.
To perform a forward lookup brute force with Nmap, you can use the following command:
nmap -sL -n <domain> | awk '/Nmap scan report/{print $NF}' | xargs -I{} host {}
By using the techniques discussed in this section, you can discover all the DNS servers and records for a particular domain.
Is DNS Enumeration Passive or Active?
DNS enumeration can be both passive and active.
Passive
Passive DNS enumeration refers to the process of collecting DNS data from various sources without directly interacting with the target network. The Passive DNS enumeration includes collecting data from public DNS servers, DNS cache snooping, and analyzing DNS traffic.
Nmap can passively enumerate DNS data by analyzing DNS traffic on the network. To collect DNS data from the target network’s DNS servers, use the “dns-nsec-enum” NSE script.
Active

Active DNS enumeration involves directly interacting with the target network to gather DNS data.
This includes sending DNS queries to the target network and analyzing the responses to collect information about the network’s DNS infrastructure.
You can use Nmap for active DNS enumeration by sending DNS queries to the DNS servers of the target network.
Use the “dns-brute” NSE script to brute force DNS subdomains and collect information about the target network’s DNS infrastructure.
Best Practices for DNS Enumeration with Nmap
When it comes to DNS enumeration with Nmap, users must follow several best practices to ensure that they are conducting their scans safely and effectively.
These best practices include using Nmap scripts, limiting scanning, and staying legal.
Use Nmap Scripts
Nmap scripts can be handy when it comes to DNS enumeration. They can automate the process and provide users with valuable information about the target’s DNS servers, domain names, and IP addresses.
Some of the most popular Nmap scripts for DNS enumeration include:
- dns-brute: This script performs brute-force DNS enumeration against a target domain.
- dns-zone-transfer: This script aims to execute a zone transfer on a specific domain.
- dns-recursion: This script checks if a DNS server is vulnerable to DNS recursion.
Limit Scanning
It is essential to limit scanning when conducting DNS enumeration with Nmap. For example, users should avoid running scans against domains they do not own or have permission to scan.
Also limit the frequency and intensity of their scans to avoid triggering any security alerts or getting banned by the target’s network.
Conclusion
Overall, DNS enumeration with Nmap is a valuable tool for professionals looking to identify potential security vulnerabilities in their networks.
By using Nmap to scan for open DNS servers and querying those servers for information about the network, you can gain valuable insights into the network’s architecture and potential points of weakness.
Now, it’s your turn to put the lessons in this article into practice. I wish all the best. Stay cultuvated.

